
As AI climbs the cybersecurity concern list, we must not neglect the continued threat of human error, warned panellists at Channel-Sec, hosted at the Forest of Arden Hotel, on 8th – 9th May 2025.
A delegate survey at the event showed that AI-driven phishing attacks are now the number one cybersecurity threat that scares MSP thought-leaders the most. With 66% of respondents placing this within their top two areas of concern, AI was positioned as the weapon of choice for both sides in future cybersecurity conflicts.
However, it was the job of our second panel to judge the entire state of the battlefield and assess where MSP focus should be shifting in 2025 to best protect UK plc.
Panelists agreed with our delegate poll that AI will play a significant role moving forward by providing an entirely new toolset for both attackers and those on the defence. Phil Guest, Chief GTM Officer at ThinkCyber, noted: “AI is an incredible tool, both in its power and its potential danger. It is a vanguard of how quickly the threat landscape is evolving and the future will be both sides staying on top of constantly iterating tools to keep the upper hand.”
To highlight the threat, one panelist discussed Worm GPT, a similar platform to readily available AI interfaces but designed for threat actors to create and deploy malware easily. “By simply copying and pasting prompts found on the dark web anyone can now build and use sophisticated malware,” they said. “This is a challenge that will require AI to combat. We are watching a future be created where AI is fighting AI.”
This alludes to the rapid speed at which MSPs are going to have to move to stay proactive and not reactive. Stephen Harper, Lead Cloud Architect at Arrow, said: “Attacks are coming multi-fold because attackers are using AI engines. In the MSP world, we have to re-arm ourselves constantly moving forward. This will mean lots more thinking about toolset, training, and education. To succeed in this space MSPs must enter a continual service improvement loop of re-arming themselves to protect their clients.”
However, Sasha Roshan, Sales Engineer at Huntress, points out that this doesn’t signal a point of no return where nothing will be the same again. He noted: “This is a new battlefield and everyone in the room can feel that, but ultimately it is the same story of good vs bad, just with a new set of tools.” He warned that we can’t let this distract us from some of the other long-lasting cybersecurity concerns.
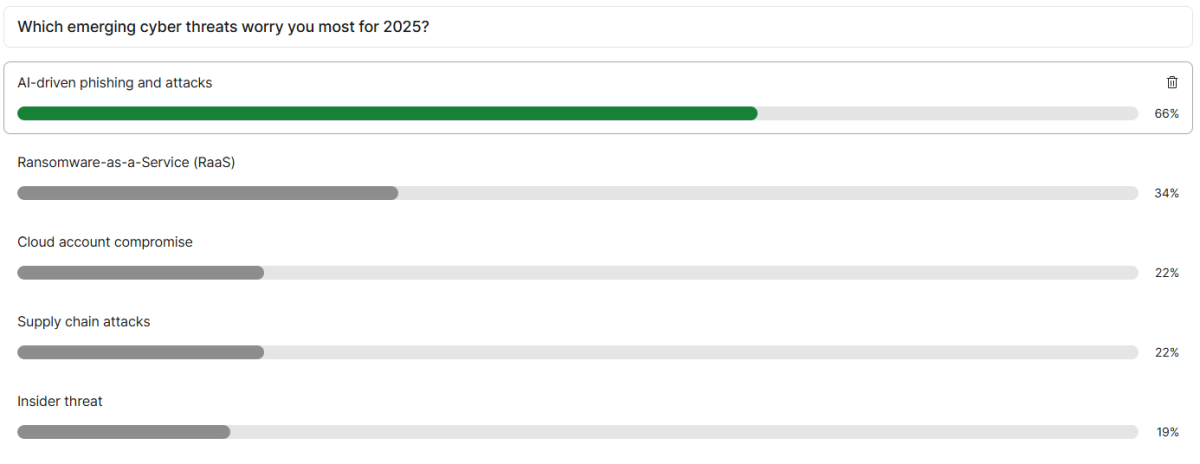
For example, the second most elevated concern was Ransomware, which 35% of delegates put in their top two concerns. Despite this being a lasting threat, it is something that many businesses still aren’t taking seriously. Paul Hooper, CEO at Uplands OneTelco, said: “Many customers still have no plan. We talk to organisations and ask if they would pay to get their data back. Most haven’t even considered it. Many still don’t understand their the data has multiple values and may still be sold on the dark web after it is recovered.”
Human error
The biggest disparity between our poll and our panelists’ concerns was the role of human error. Despite only 19% of delegates listing ‘insider threat’ as a top two concern, our experts elevated this to the forefront of discussion, highlighting that many insider incidents don’t come from malice, but instead from ignorance or fatigue.
To support the severity of our panelists’ concerns, around 95% of data breaches in 2024 had a level of human error as a contributing factor, according to Mimecast research released earlier this year. The same research found that despite most (87%) organisations claiming to train their employees to spot cyberattacks at least once a quarter, 33% fear mistakes and human error in handling email threats by employees, and 27% are concerned that fatigue is causing lapses in vigilance.
Matt Frye, Head of Pre-Sales at Hornetsecurity, pointed to the outdated nature of training as a major cause for cyber-attacks. “The current state of training at most companies is not compelling, interesting or useful. It is a process of having staff click through pages, take nothing in and schedule in another hour in the coming quarter. Engaging and informative training is the bedrock for combating threats, but it is about how it’s delivered and when it’s delivered.”
Being fed technical information also leads to security fatigue. Guest highlighted: “The fastest growing area of insider threat comes from errors caused by this security fatigue. Staff are busy doing their jobs and cyber attackers have a knack for hitting staff when they are at their lowest. This fatigue also creeps in regarding the use of tools. Roshan said: “You’ve got to make software and processes usable as the fatigue will cause end users to look for workarounds that sidestep or remove blocks. This leads to shadow IT which is a massive attack vector for criminals.”
Hooper shared how he has overhauled training at Uplands OneTelco. He shared: “We used to follow the typical system of force-feeding information to new joiners and then doing regular refreshers and calling it a day.
“Our new system revolves around making conversations accessible and relatable. For example, M&S has done a great education campaign for us, and we will now host an off-the-cuff session telling our staff the story of what happened and where it could happen to us. From an awareness point of view in your team, a conversation about a real-world case can do much more than a best-practice leaflet.”
Frye points out how a mindset shift is needed from seeing security as a tick box exercise to focusing on the human element. “Companies are doing the bare minimum but aren’t actually making themselves secure.”
Filling in the gaps
MSPs need to lead this charge from the front and drive the education piece, according to Roshan. He notes that education for staff is one of the main desires that resellers have when forming new partnerships. He said: “They want small customers to come on board but are struggling with the practical conversations which require a level of skill and knowledge to properly convey the value proposition.”
The other facet of this is ensuring their portfolio is fit for purpose. Frye stated: “Most of the time it’s about modernising what they are doing today to make sure it is fit for purpose. There is a lot of tech out there and some of it is really aged and should be retired. This isn’t going to help with the human error piece.”
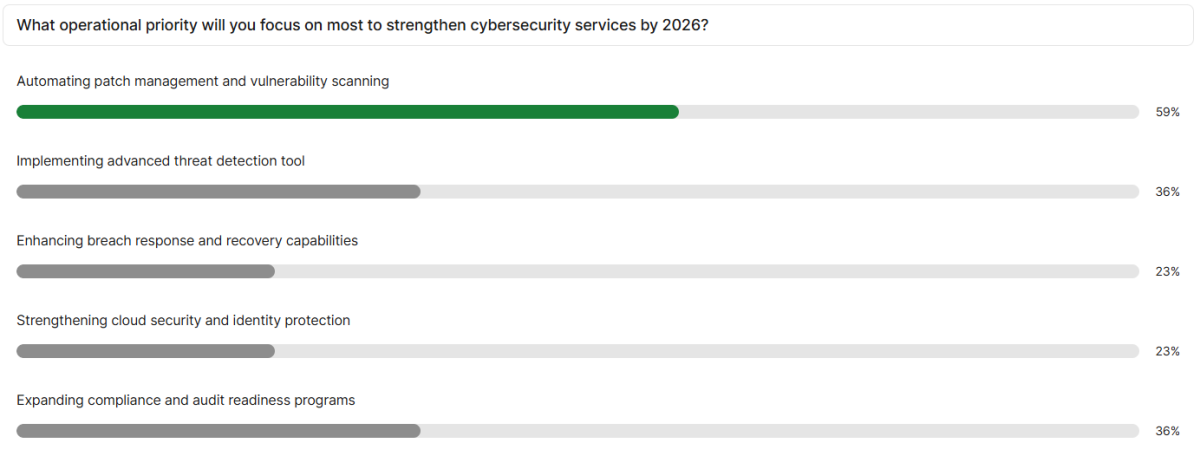
A second delegate poll explored what the operational priorities will be for MSPs looking at strengthening cybersecurity portfolios in the coming years. ‘Automating patch management and vulnerability scanning’ was top with 59% of respondents selecting this in their top two, Enhancing breach response and recovery capabilities, and expanding compliance and audit readiness programmes were joint second, featuring in the top two for 36% of delegates.
Roshan finished: “Once the education and portfolio pieces are in place, it is about getting the right strategy in place. Cybersecurity is wide and evolving so there is always an opportunity to take partners to the next level. This is especially relevant in the vast SME market. Prove value and help them understand why cybersecurity is a necessary investment.”



